Can ransomware spread through WiFi?
Can ransomware spread through WiFi? Yes, it’s possible.
Citing Wikipedia: “Ransomware is a type of malware that threatens to publish the victim’s personal data or perpetually block access to it unless a ransom is paid.
Ransomware attacks are typically carried out using a Trojan, entering a system through, for example, a malicious attachment, embedded link in a phishing email, or a vulnerability in a network service.”
This type of malware has become one of the first threats in the cybersecurity landscape of several industries.
Several reports have shown how MSPs, ISPs, and SPs remain prime targets for those attacks. The reason is simple: their business model serves many SMBs, medium and large enterprises, with multimillion assets attracting the interest of hackers. The most common ransomware that attack MSPs are CryptoLocker, WannaCry and CryptoWall.
In its last report about network security, Cybersecurity Ventures has estimated that “every 2 seconds, a ransomware attack occurs. The expected global damage costs by 2031 will be around $265 billion”
It is easy to understand how the growth of damage occurs in parallel with the growth of downtime, caused by increasingly sophisticated ransomware.
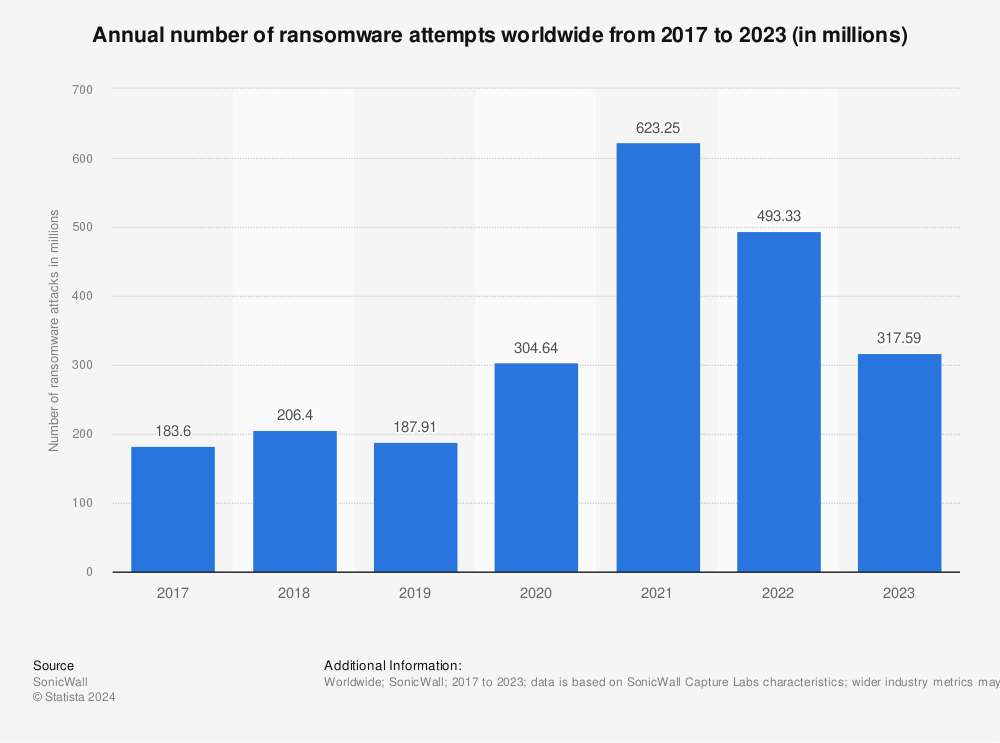
A 2023 study by Statista confirms that “Although ransomware still ranks behind other more concerning malware types such as viruses and trojans, it has huge potential for damage – both for businesses and individuals alike. In fact, the annual share of ransomware attacks experienced by organizations worldwide has been on the rise since 2018, peaking at 68.5 percent in 2021.”
Annual number of ransomware attacks worldwide from 2016 to first half 2022 (in millions)
The threat of ransomware is not always related to software download or email phishing. The increase of global network traffic and the economical interests of hacking groups during post-Covid19 and Russia / Ukraine war have multiplied the types and quantity of attacks against business networks. Wi-Fi networks can become a vector for traditional ransomware.
There are ransomware categories, such as Emotet, that operate as worms bypassing the weakest passwords and infecting multiple contiguous wireless networks. There are ransomware, such as Chameleon, that collect and report the credentials of all other WiFi users who connected to it. And then, they try to expand the infection other WiFi APs that they could connect to and infect.
It’s basically impossible to defend WiFi networks from every type of ransomware. The correct approach that MSPs, ISPs, and SPs should have in this complex scenario of malware threats is to adopt the best defense technologies against ransomware in relation to Wi-Fi.
What is a possible defense for business networks against Wi-Fi ransomware?
Tanaza suggests Configuring RADIUS Authentication + NAS ID with WPA-Enterprise.
For instance, let’s analyze the behavior of the ransomware Chameleon to understand the approach used by Tanaza to fight ransomware attacks.
The goal of this ransomware is data theft, device malfunctions at the OSI layer 2, and the lock of lists of files or entire systems for ransom reasons when integrated with worms.
The first malicious portion of the code of this ransomware executes a deep network scan to discover possible susceptibilities into the access points. Scanned vulnerabilities include weak passwords, outdated firmware, and unsafe encryption protocols of the Wi-Fi device (as WEP, WPA, WPA+TPKI, WPA + TKIP/AES, WPA + AES). When the ransomware finds access points with easy to crack passwords (appealing for dictionary attacks) or unsafe network protocols, the ransomware can bypass the security protocols and the administrative interface of the access point.
At that moment, Chameleon identifies and stores AP system settings, replacing the original firmware with a virus-loaded and reloading the new malicious AP settings.
The activity of malware is unstoppable. The propagation of ransomware would continue despite upgrades to security methods, such as deep packet inspection or the change of security protocols in a second moment. The malware could infect other nodes. The propagation would continue near weak networks on an infinite loop.
Threat prevention against WiFi ransomware
The configuration of the RADIUS Authentication server + NAS ID with WPA-Enterprise represents a triple level of security for MSPs, ISPs, and SPs.
When a user tries to authenticate to the network, he fills the fields with a username and password to execute the login. The device creates an Access-Request message and sends it to the preconfigured RADIUS server. In this message, there are the encrypted credentials. The Radius server will confront the received login credentials with the data on an internal database to establish if the client is known.
If the device is a client known to the RADIUS server and the shared secret is correct, the server looks at the authentication method requested in the Access-Request message. If not, the RADIUS sends an Access-Reject message that shows authentication failure. The RADIUS communication ends and the client is denied access.
At this level, the MSPs, ISPs, and SPs network have solid protection standards because, during the network scan by malware to find AP susceptibilities, the ransomware should crack the WPA Enterprise AES-CCMP protocols (bypassing robust cryptography techniques: “counter mode” and “CBC-MAC”) and intercept the Access-Request message, falsing it with the list of credentials into the database.
What is WPA Enterprise?
WPA Enterprise is one of the safest WiFi security methods for network protection. The protocol was specifically designed for the network defense of business organizations. The encryption method used by this security protocol is AES-CCMP: it encrypts data transmitted over the air.
WPA Enterprise is used in MSPs, ISPs and SPs environments where design protection system againts Wi-Fi ransomware is critical. This security protocol uses the IEEE 802.1X standard for network access control, which provides an authentication framework for devices attempting to connect to the network.
In WPA Enterprise, when a client attempts to connect to the network, the access point requests authentication credentials from the user’s device. The device then sends the credentials to an authentication server for verification. If the credentials are valid, the authentication server sends a message back to the access point, allowing the user’s device to connect to the network.
WPA Enterprise also uses encryption to protect the data transmitted over the network. It supports multiple encryption methods, including the Advanced Encryption Standard (AES) and Temporal Key Integrity Protocol (TKIP).
What is RADIUS Authentication?
Remote Authentication Dial-In User Service (RADIUS) is a client/server protocol and software that enables remote access servers to communicate with a central server to authenticate dial-in users and authorize their access to the requested system or service.
And if the authentication fails on the primary server?
Tanaza has enabled a secondary server feature. As for the first one, it’s possible to configure IP addresses or hostnames, ports, and shared secrets (password, passphrase, or a number).
How to configure radius server for wireless authentication?
For best performance and network security, Tanaza suggests having the RADIUS server and gateway access points located within the same layer-2 broadcast domain to avoid firewall, routing, or authentication delays. Another interesting feature that MSPs, ISPs, and SPs can use as a security method, it’s to set the NAS ID.
NAS ID – Network access server identifier
NAS ID is the further protection technology developed by Tanaza to protect networks from ransomware. NAS ID is textual code that enables the RADIUS server to choose the policy for that specific request. The NAS-ID is sent to the RADIUS server by the centralized platform through an authentication request to classify clients into different groups and subgroups. This enables the RADIUS server to send a customized authentication response.
Network segmentation security through SSH access of APs
Above, we have analyzed how Radius Server Authentication and WPA security protocol are solid protection against ransomware for SSIDs security.
Tanaza offers another level of protection at the AP level: SSH access.
SSH protection provides IT and information security professionals with a solid mechanism to manage clients remotely. Rather than requiring password authentication to initialize a connection between an SSH client and server, SSH authenticates the access point themselves.
Operators can enable SSH access on different granularities of the segmented network:
– for each single access point;
– for the entire network through the feature network-wide configuration.
Remember for a second the aforementioned ransomware Chameleon and its malicious action of network scanning to find APs susceptibilities in order to replace the original firmware. The SSH encryption protocol is a further robust shield to avoid AP intrusions and firmware modifications. When SSH is enabled, the access point is protected by the highest compliance requirements related to SSH keys.