Capterra has awarded Tanaza in Capterra Shortlist 2022 as Emerging Favorite in Network Monitoring Software

Capterra has awarded Tanaza in Capterra Shortlist 2022 as Emerging Favorite in Network Monitoring Software
The prestigious Capterra – a Gartner Property – has awarded Tanaza in the Capterra Shortlist for Network Monitoring Software category.
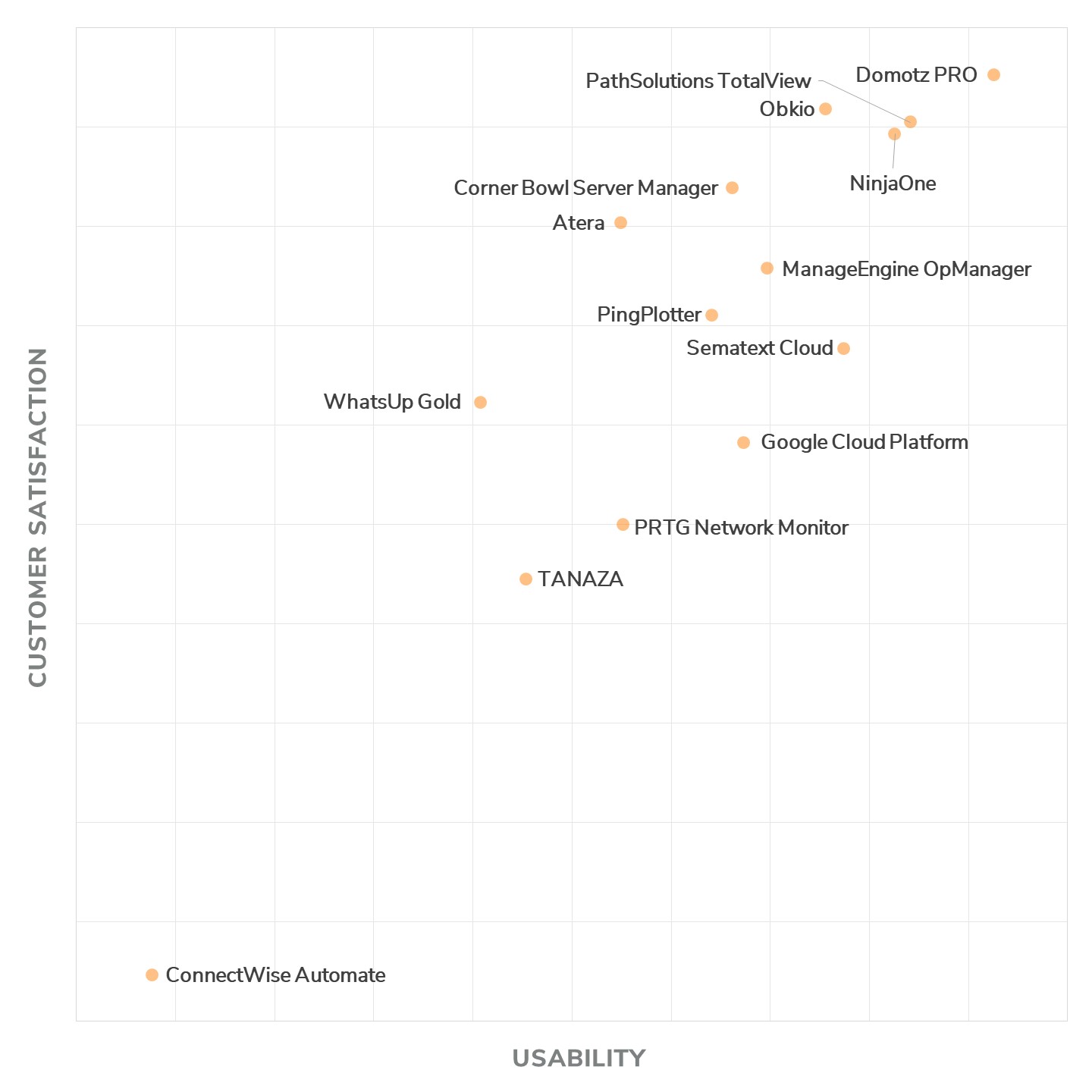
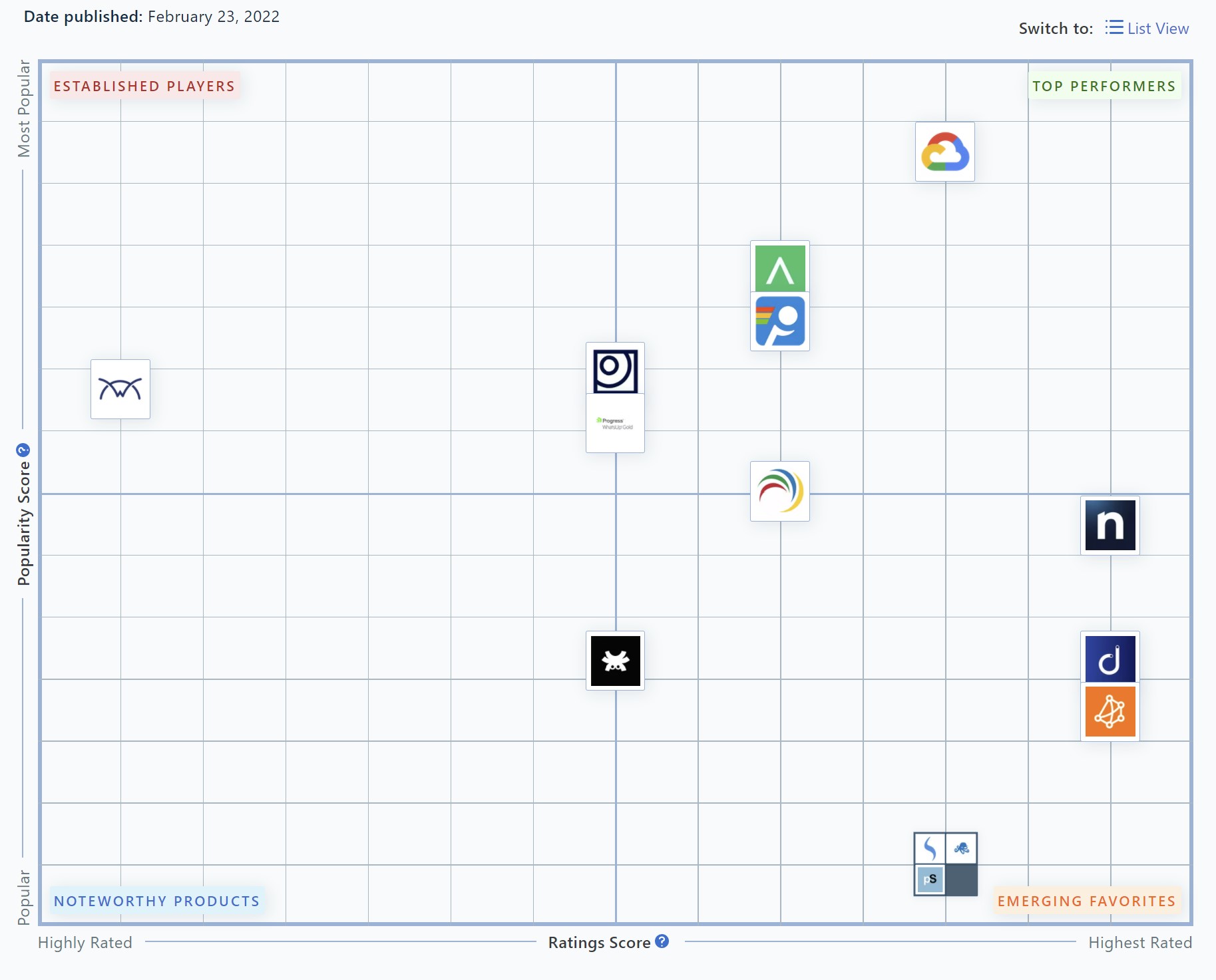
This important award allows Tanaza to become Emerging Favorite 2022 Network Monitoring Software with the main network cloud solutions of the market, including Google Cloud Platform, PRTG Network Monitor, ManageEngine OpManager, Atera, Domotz PRO, NinjaOne, WhatsUp Gold and PintPotter.
What does Capterra Shortlist consider to draw up the Network Monitoring Software’s Emerging Favorites list?

Emerging Favorites are products that rate highly in satisfaction (sometimes even higher than the Top Performers) but aren’t as well known as the Top Performers.
Today, Tanaza has earned a score of
4.5 / 5 (70) ⭐⭐⭐⭐⭐
The Capterra Shortlist methodology scores vendors on two dimensions: User Ratings and Popularity.
- The Ratings component is plotted on the X-axis and considers the overall user ratings of products based on reviews written in the last 24 months. Users rate products on a scale of 1 star (lowest) to 5 stars (highest).
- The Popularity component is plotted on the Y-axis and considers average monthly search volume for a standardized set of keywords for each product, as derived by a proprietary search methodology, as well as the position of the vendor’s domain on the search engine results page (SERP) for each keyword. This is a measure of user interest and relevance used as a proxy for popularity.
Each score (Ratings and Popularity) is weighted and scaled to a value between 1-50.
Data sources include approved user reviews, public data sources and data from technology vendors.
What is Tanaza?
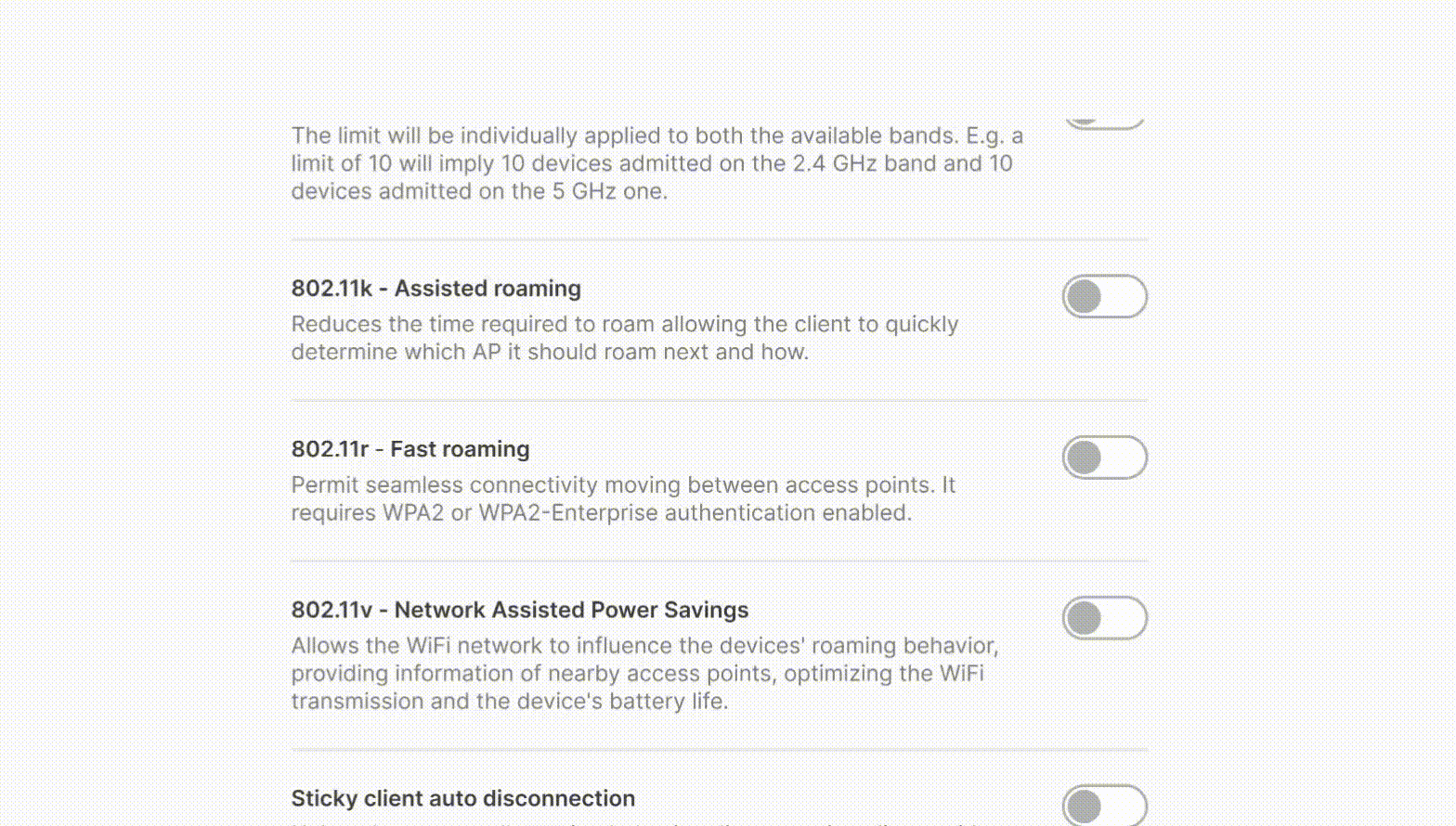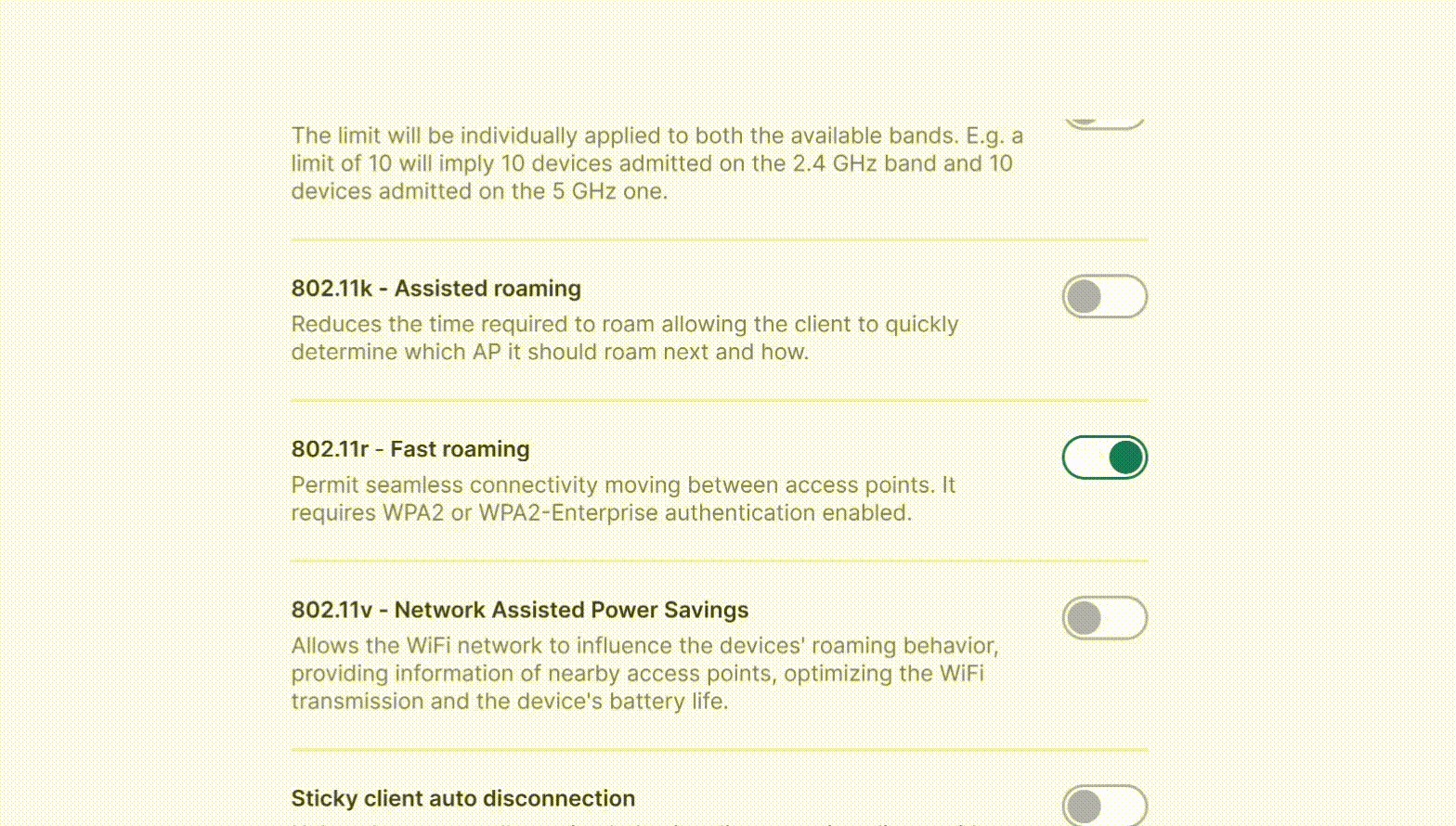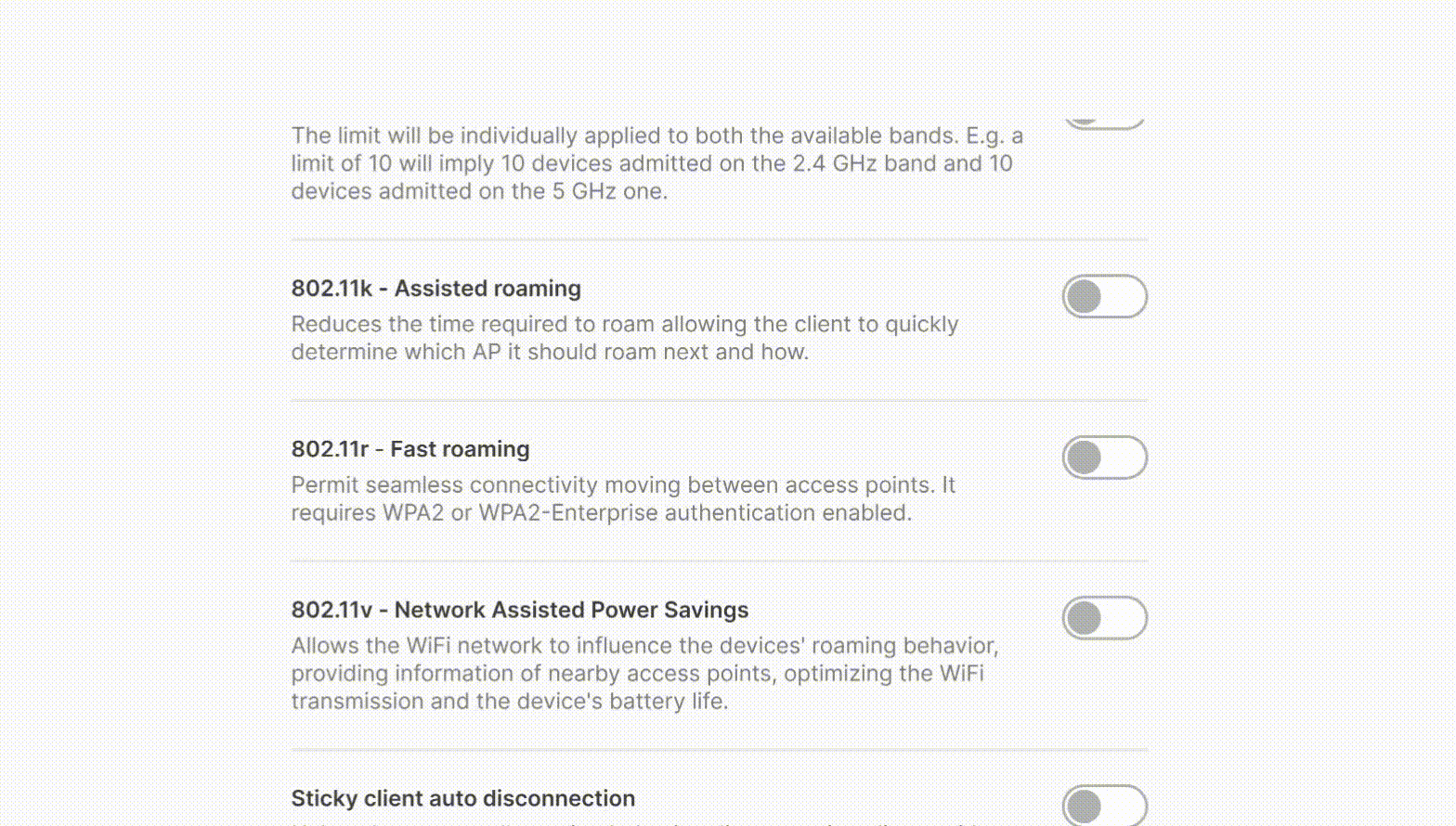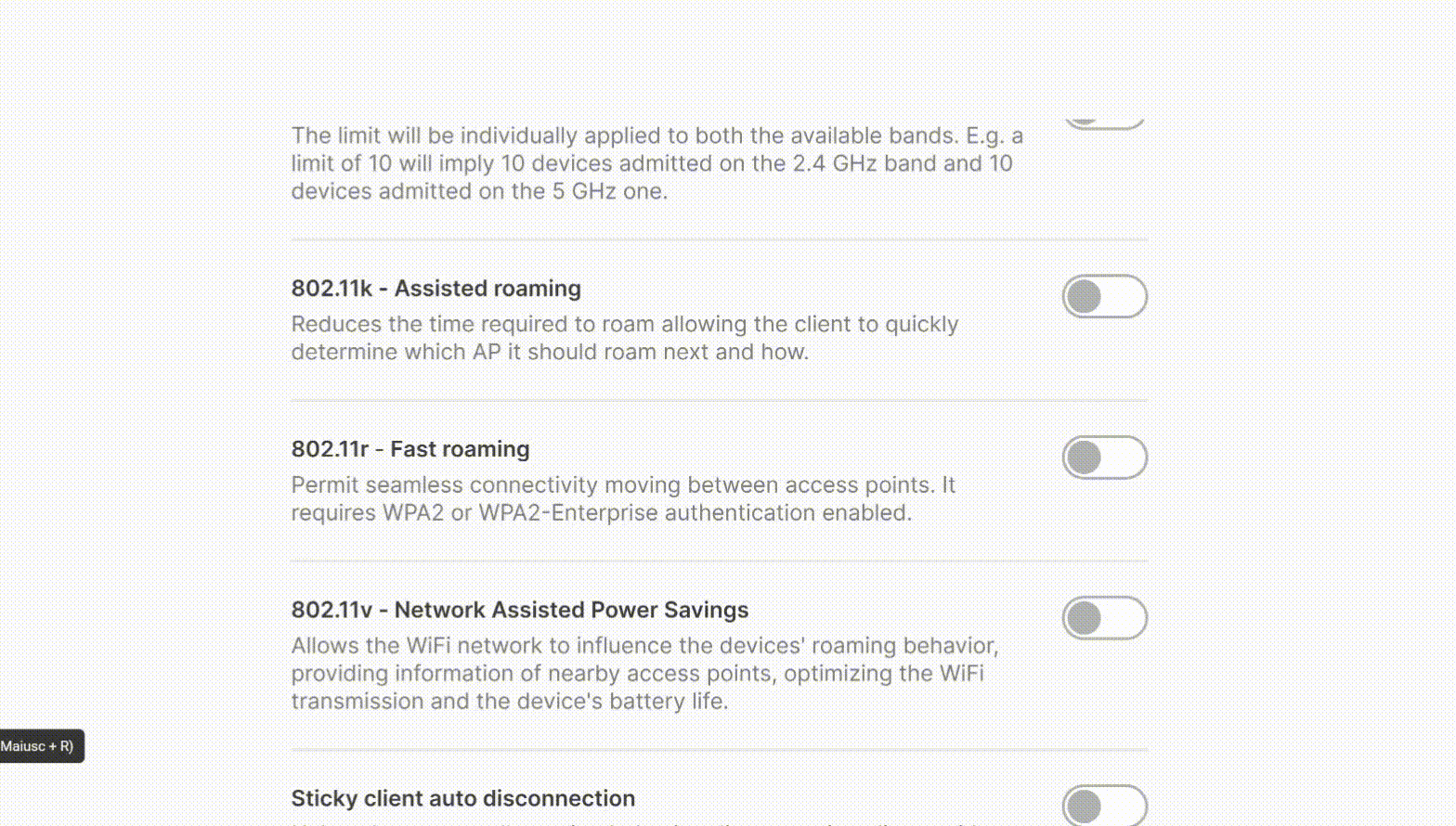
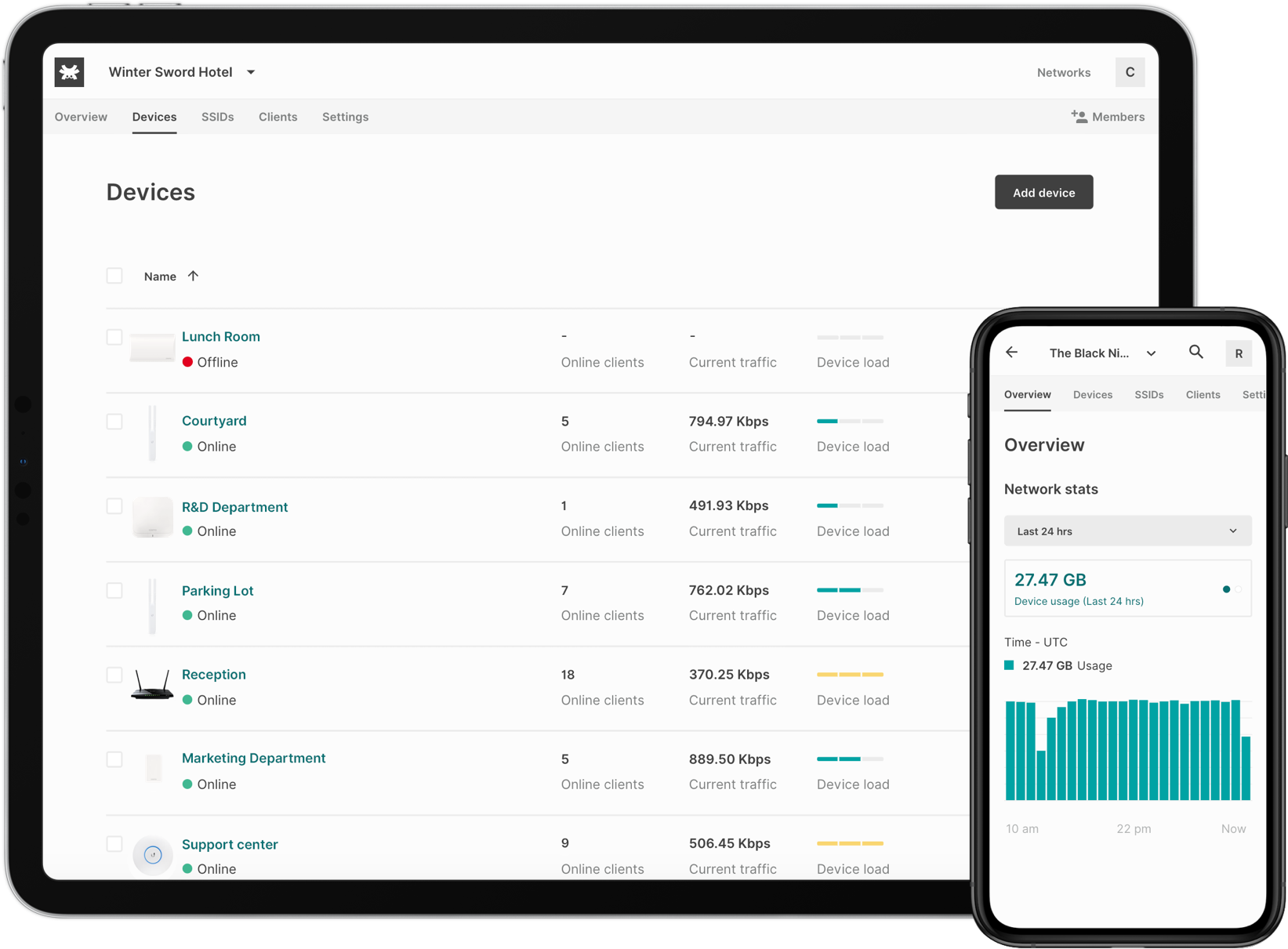
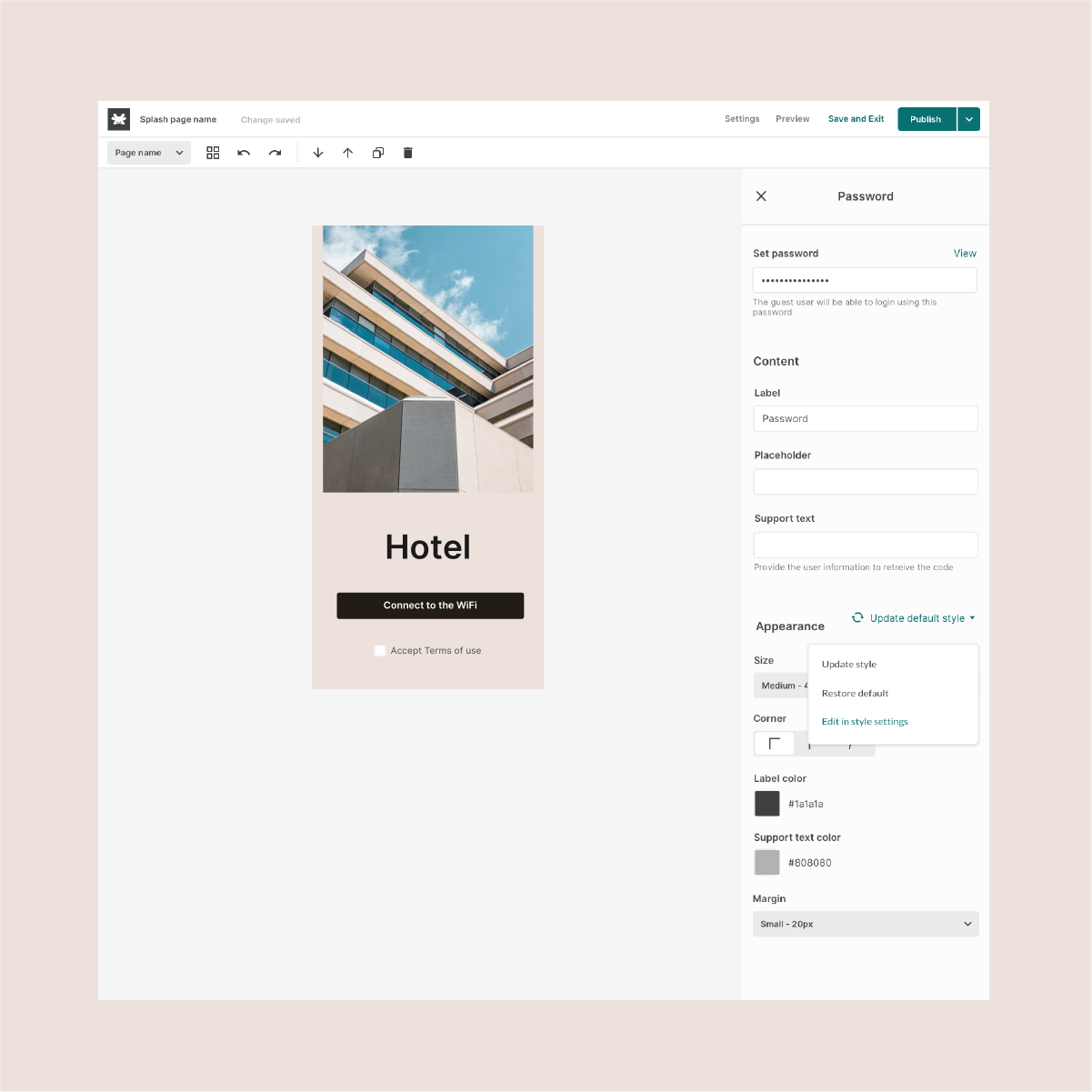
Tanaza allows organizations to manage service set identifiers (SSIDs), provision devices for customers and track available inventory on an administrative dashboard. Supervisors can create and design customizable authentication pages to improve and enhance guests’ WiFi experience. Other features include geolocalization, network configuration, scheduled reboots, access point management, WPA2/WPA2 authentication, bandwidth control and more.